Email remains a staple of business communications, but the use of social media and mobile messaging apps on employees’ personal devices has grown exponentially. This evolution in communications has driven a fundamental change to the threat landscape and is putting new pressure on security operation centers (SOC).
SOC teams need to be able to identify and respond to new, more sophisticated social engineering attacks across all the cloud channels used in their organization. Having greater visibility into social media, collaboration, and conferencing communication channels is a must for a future-proof risk prevention strategy.
In a recent blog post, Forrester emphasizes how everything in detection and response starts with the security operations center (SOC). “Focusing on improving the analyst experience (AX),” they say, “security professionals can find more effective security tools, build better workflows and help security analysts make faster, more accurate decisions.”
To increase their efficiency and effectiveness in today’s threat environment, SOC teams and analysts need their tools to offer greater intelligence for threat identification and remediation. In addition, these new tools must be able to integrate quickly and easily with new cloud communications channels through APIs instead of agents that require ongoing maintenance.
Disrupting the Business Communications Compromise Attack Chain
Attackers typically start with email phishing as an entry point into a targeted business. If their phishing attempt is successful, they quickly move the conversation to cloud channels such as Slack or Teams. Using social engineering techniques such as impersonation, they gain access to the corporate network to deliver a ransomware attack, create phony invoices, or steal company IP that is sold on the Dark Web.
In general, home offices are inherently less secure than traditional office environments, and attackers are quickly taking advantage of these opportunities. While business email compromise (BEC) still happens regularly, it’s only one part of a larger threat -- business communications compromise (BCC.)
Protecting businesses and employees in today’s highly distributed environment has become an increasingly complex challenge. SOC teams need better, more intelligent solutions to gain control over an expanding attack surface and become more efficient in their efforts to stem the growing tide of attacks.
Increasing SOC Efficiency and Effectiveness
In some organizations, SOC teams have adequate budget for good tools, enough staff to manage them, as well as executive support and executive visibility. But many SOC teams are limited in their response to threats by being understaffed, constantly operating under time constraints, and held back by inadequate visibility into active and emerging threats. For these reasons, it’s essential for SOC teams to focus on deploying intelligent tools that can help them use their skills more effectively and adapt quickly to future threats across new communication channels.
While increased visibility is critical to ensuring a good defense against attacks, the ability to understand the context and intent of messages – in both directions – is needed to prevent BCC from impacting your organization. The human element in social engineering and language-based attacks can be difficult for many SOCs to identify and interpret, so support is needed from intelligent, ML-based tools.
|
82% |
83 million |
45% |
|
Source: Verizon Data Breach Investigations Report |
Source: Microsoft Cyber Signals |
Source: Business Communications Report 2022 |
Future-proofing Risk Defense with Natural Language Understanding
Although legacy network tools and solutions like firewalls and endpoint detection and response can prevent some attacks, such as malware. But to disrupt social engineering and phishing attacks early, especially during the initial compromise phase, the use of Natural Language Understanding (NLU) is helping cybersecurity teams and professionals become more effective in their threat defenses.
NLU technology deployed in SafeGuard Cyber security looks inside messages delivered across multiple communication channels and analyzes the intent and context of the conversation itself. It detects language-based threats that traditional security technologies weren’t designed to detect.
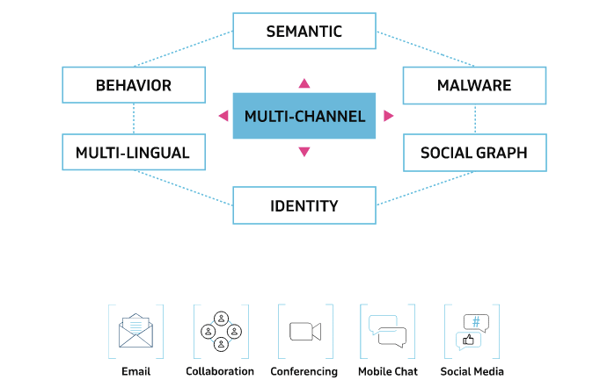
SafeGuard Cyber helps security teams protect their business communications from social engineering,
phishing, insider threats, and language-based attacks that evade legacy solutions.
Traditional cybersecurity tools that rely on metadata-based behavioral analysis can identify unusual activity, but NLU analyzes the language-based elements in conversations, including lexical features, context, and topical elements, and automatically analyzes and evaluates messages against models to identify and prevent social engineering and language-based attacks.
With visibility across multiple communication channels and NLU analysis of context and intent, organizations can respond faster and stop attacks earlier in the kill chain. By constantly evaluating messages and adding new data to its threat analysis core, SafeGuard Cyber security can provide better protection against threats faster and more intelligently to help SOC teams improve efficiency and threat defense. And with the ability of SafeGuard Cyber security to integrate quickly into new channels via APIs, eliminating the need for agents, it delivers future-proof security against today’s and tomorrow’s threats.
If you are interested in learning more about the SafeGuard Cyber solution, you can take a quick 5-minute tour.

