A recent Fortune article found that numerous US government employees are using their LinkedIn profiles to promote their access to top-secret information, including Top Secret/Sensitive Compartmented Information (TS/SCI) clearance, which is one of the highest levels of security and a focus of the FBI’s ongoing investigation into former President Donald Trump’s handling of classified information taken from the White House.
Individuals who promoted their security clearance level on LinkedIn come from a mixture of government, military and private sector jobs, and, according to Fortune, accepted connection requests from a complete stranger with no questions asked. By disclosing their security levels, LinkedIn members are increasing their risk of becoming a target of attackers, specifically from nation-state actors.
Sharing confidential information, such as security clearance, is essentially an open invitation for threat actors to use every trick in their book to impersonate the poster, steal credentials, launch a malware attack, or simply for financial gain. Security practitioners need to be able to identify threats in real time and take appropriate action to prevent these threats from doing damage. And since LinkedIn is only one of many cloud communication channels in use today, it’s critical to monitor multiple channels in real-time to stop these types of damaging breaches.
According to Katherine Gronberg, Head of Government Services at NightDragon, “Individuals who post security clearance information on social media sites make themselves an easy target for adversaries. Attackers already leverage AI-controlled bots to scrape social media sites for information like this. But there’s no need to make it even easier for them.”
“By openly sharing their security clearance levels, LinkedIn users can put themselves in danger of being impersonated or becoming involved in a social engineering attack,” said Chris Lehman, CEO of SafeGuard Cyber. “We’re seeing a steady increase of language-based attacks that use impersonation, deception, urgency, and semantic tactics to convince their targets to take actions that they shouldn’t – actions that are dangerous when it comes to national security. This is why our ability to determine the context and intent of messages is critical in identifying attacks that use impersonation.”
With its patented Natural Language Understanding capabilities, SafeGuard Cyber executes queries across large volumes of data in more than 30 channels of communications, including LinkedIn. Even when messages have been deleted, the SafeGuard Cyber platform can identify threats in erased digital content and prevent breaches. With these capabilities, organizations can be protected from the same threats that the government is combating today.
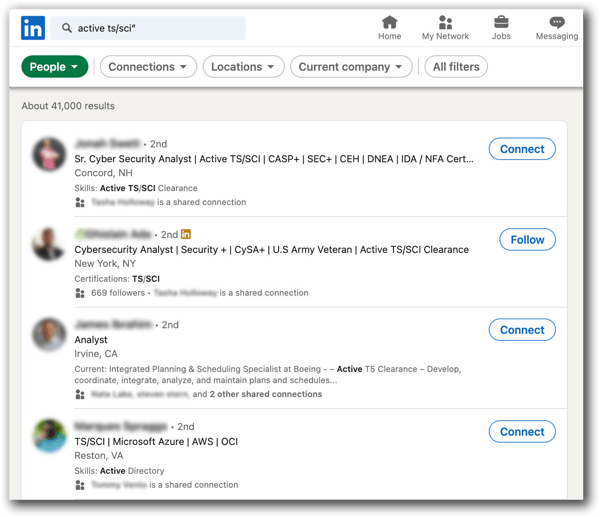
Searching for “Active TS/SCI” clearance on LinkedIn brings up 33,000 users. Only a fraction of those identified will have an active TS/SCI, but the first 5-10 pages of people are easily targeted.
If you are interested in learning more about the SafeGuard Cyber solution, you can take a quick 5-minute tour.
