The throes of the “Great Resignation” are still with us, and now we have economic conditions that may lead to recession. Budgets are starting to tighten, inflation is rising, interest rates are up, and many companies – which may include yours – face uncertainty and anxiety in their workforce operations. This uncertainty takes many forms:
- Churn: in some places, employees are still headed for the doors, often for positions at competitor organizations
- Employee anxiety: according a recent LinkedIn poll, hiring freezes and news headlines have employees worried and anxious about their jobs
- Overtaxed workers: whether it’s announcements of hiring freezes or an inability to fill current vacancies, current employees are being asked to do more with less
All of these conditions put the focus on the role of insiders in your company’s security posture. Be it malicious or accidental, human end users are behind all your systems and data, and therefore, employees can quickly threaten your organization’s data, personnel, equipment, networks, and systems. Insider threats can cause costly damage to an organization, even more than malware and ransomware attacks. The 2022 Ponemon Cost of Insider Threats Global Report notes that insider threat incidents have risen 44% over the past two years, with costs per incident averaging $15.38 million each.
This post will look at the post-pandemic work conditions that necessitate new ways to mitigate insider threats. Moreover, we’ll examine the limitations of legacy tooling to meet the needs of today’s cloud-driven workspace.
The Cloud Workspace Changes How Employees Communicate
With the rapid increase in cloud infrastructure to support workforce operations, it’s become critical that security teams have insight into the the context and intent of communications. For example:
- Is that email really from the CEO?
- Is that Slack message asking for credential reset related to an email?
- Is that MS Teams chat related to access legitimate or malicious?
Moreover, can the SOC correlate risks that occur in multiple communication channels? Most security tools are focused on payloads and penetration from external actors. And, existing insider threats tools rely on heavy endpoint agents to detect file movement. These legacy tools can be difficult to manage, especially with a proliferation of BYOD endpoints. Cloud channels like Slack and Teams are accessible via browser tabs and via apps on personal devices where agents can be impossible to install. Additionally, agents on just corporate endpoints often result in serious drag on network compute power.
Current State of Insider Threats
The increasing complexity of business communication systems means it’s harder for security teams to detect and respond in a timely manner. The time to contain insider threat incidents grew from 77 days in 2020 to 85 days in 2021. Only 12% of insider threats were contained within 30 days, and 34% took more than 90 days to contain. The Ponemon report also reveals that:
- 14% of all insider threat incidents are the result of malicious insiders
- 62% are the result of negligent insiders and are the most common incidents
- Negligent Insiders who have their credentials stolen account for 25% of all incidents
- The cost of credential theft to organizations increased 65% from $2.79 million in 2020 to $4.6 million today
- Incidents that took more than 90 days to contain cost organizations an average of $17.19 million annually
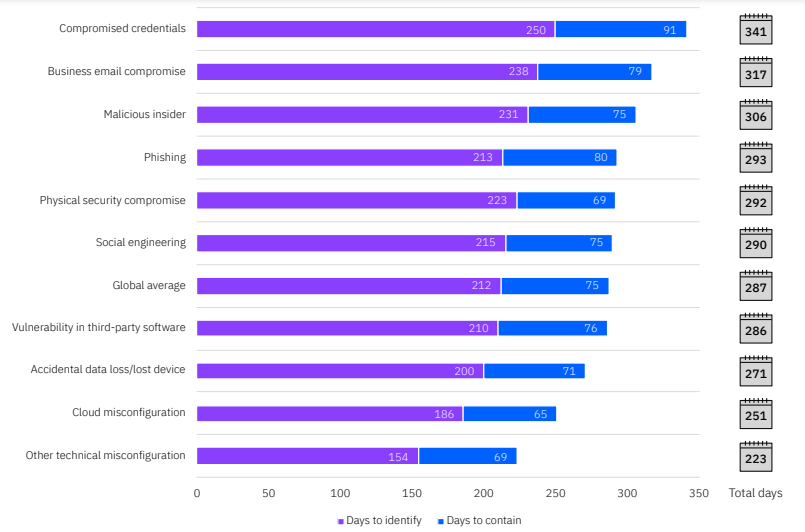
Average time to identify and contain a breach by initial attack vector.
Source: IBM Security
With threats moving beyond email to the cloud workspace, it’s become critical for organizations to monitor both inbound and outbound communications across email, collaboration, mobile chat, and social media channels. Analyzing threats against risk signatures such as topics, behavior, lexicon, and more can help prevent insider threat scenarios, social engineering attacks, ransomware, and policy violations.Examples of Insider Threat Incidents
Ransomware/cybercrime recruitment
In late 2021, a survey of 100 IT and security executives conducted by Hitachi ID revealed that hackers had approached 65% of executives or their employees to assist in ransomware attacks, with most using email as their main threat channel. The threat actor apparently collected employee contact information from LinkedIn to find potential accomplices. Using email, the external attacker offered the targets two contact methods — an Outlook email account and a Telegram username — where they could discuss proposed attacks and payment methods.
In another widely-reported attack, the DemonWare ransomware group attempted to bribe employees via email to install ransomware on their employers’ networks. The group promised to pay company insiders $1 million in bitcoin if they installed the malware on their employers’ networks.
From 2012 to 2017, AT&T suffered $200 million in lost subscriptions when Pakistani resident Muhammad Fahd was successful in bribing call center employees to install malware on the company’s systems. The malware automated the unlocking of 2 million AT&T iPhones.
IP/data theft
Data breaches that involve an organization’s intellectual property (IP) can have a tremendous business impact, as much as breaches that involve records and data theft. Organizations can suffer from losing patents, trademarks, copyrights, trade secrets, and other confidential information.
In 2019, the FBI revealed the details of a theft of intellectual property and trade secrets by two employees from 2011 to 2012. In this theft, the perpetrators downloaded trade secrets for GE turbines as well as cost models, proposals, and contracts. Using this information, they were able to operated a company that undercut GE’s pricing for years.
In another example, an employee at insurance software developer Vertafore stored the company’s data files in an unsecured external storage service. The files contained information from millions of Texas driver’s licenses, and the company is now facing a potential class action suit from this inadvertent breach.
Trade secrets have also become popular targets for insider theft. The Chicago-based popcorn giant, Garrett Popcorn Shops, had more than 5,400 files stolen by a former director of research and development. By copying company data onto a USB drive and sending emails to her personal email address, the thief was able to steal the company’s popcorn ingredients, recipes, formulas, and methods.
In a recent report from Aberdeen, they found that 75% of organizations don’t have consistent, centralized visibility into their environments. Most of the organizations surveyed lack the tools needed for visibility into file movement and are unaware how often valuable files become exposed by legitimate users carrying out their day-to-day activities.
SafeGuard Cyber offers strong protection against data theft and social engineering attacks with out-of-the-box and customizable detection policies. Cross-channel event correlation detects sophisticated multi-channel attack campaigns to steal IP and corporate data and malicious links and malware attachments. Policy enforcement rules within the platform monitor communication with outside parties, helping to prevent further losses.
(Mal) Activist employees
The COVID-19 pandemic has been identified as one of the main reasons that insider activists have become compelled to lash out in the workspace, targeting their employer. From physical threats and backlash relating to social and political issues and vaccination requirements, employers continue to encounter significant conflicts between management and employees.
In one example, a former software engineer at AWS caused a major breach at Capital One, an AWS customer. By misconfiguring the company’s firewalls, they were able to steal and disseminate information from approximately 100 million credit card applicants and card holders.
Last year, a former employee of a New York credit union took advantage of the company’s failure to remove her account by deleting 213 GB of company data, including mortgage applications and anti-ransomware software. The attack took only 40 minutes for her to complete.
The 2022 State of Proactive Intelligence Report from the Ontic Center for Protective Intelligence found that organizations' lack of protective intelligence contributed to numerous missed threats during the past year. Disgruntled employees have found many ways to damage companies, from leaks of company insider information to the press, to doxxing, sabotage, and more.
Rebecca Morgan, deputy director of the National Insider Threat Task Force at the National Counterintelligence and Security Center (NCSC), noted that the pandemic created a unique risk environment. “We have a risk environment where we have an incredibly stressed-out workforce. People are dealing with financial insecurity, medical and mental health isolation, and then trying to accomplish a mission simultaneously."
Organizations need to be able to identify restricted data when it crosses boundaries to head off damage caused by activist employees. With visibility into more than 30 communication channels, SafeGuard Cyber secures employee interactions and engagement in the cloud workspace, enforcing data loss prevention policies and preventing users from intentionally or unintentionally exposing organizational data.
Accidental data leaks/compliance violations
Last year, the accidental misconfiguration of an API in Microsoft Power Apps portals to allow public access caused multiple data leaks ranging from governmental bodies in Indiana, Maryland, and New York City, to private companies like American Airlines, J.B. Hunt, and Microsoft. In all, losses totaled 38 million records across all portals.
Simple negligence can also play a role in instances of lost data. For example, a former IT employee for the City of Dallas deleted over 22 TB of information from 2018 to 2021, including 13 TB of police files containing photos, videos, and case notes. While the case is still being investigated, the incidents may have involved a failure to follow procedures while conducting major file transfers.
Although a breach may be accidental, it’s still a breach and remains a threat to an organization’s health. These types of breaches range from emailing a file to the wrong person or email address, to accidental sharing of confidential files through services such as Box. With increasing access to company data hosted in the cloud, it’s critical to deploy policies to control how users share and save data without risking intentional or accidental data leaks.
The SafeGuard Cyber platform integrates via APIs directly into 30 workspace communication channels. Its patented Natural Language Understanding (NLU) technology and cloud-based machine learning (ML) detect security incidents and compliance violations in 52 languages. All data passing through communication channels are subjected to policy supervision in real-time, with automated quarantine when needed. Data is secured, and compliance violations are reduced.
Account Takeover (ATO)
One of the most feared attacks is an account takeover. Although technically not considered insider threat incidents, account takeovers involve threat actors who steal account data to resell on dark markets or make unauthorized transactions. Hackers steal login credentials through phishing, malware, and man-in-the-middle attacks, allowing attackers to take over a victim’s account by resetting passwords or accessing tokens that make requests to resource servers. With a single combination of credentials, attackers can access multiple accounts.
Prevention: Visibility & Correlation
Uncertainty and anxiety among workforces coupled with increasing complexity of the business communication environment means insider threats are harder than ever for security teams to stop. Security tooling can’t address macroeconomic conditions, but it can apply technological solutions to help SOC teams detect risks and take action. Teams need:
- Unified Visibility across their organization’s communications environment. With one place to example communication risks and trends, SOC analysts aren’t stuck in “swivel chair mode,” trying to chase threats across myriad communication channels.
- Cross-Channel Event Correlation to understand how multiple communications and risks are related. This helps reduce MTTD from days and weeks down to minutes.
SafeGuard Cyber provides security for human connections so enterprises can trust modern communications. With patented Natural Language Understanding technology and cloud-based machine learning, our security and compliance solutions deliver comprehensive visibility, detection, and response to threats and risk across the disparate communication methods used by today’s digitally enabled businesses.
If you are interested in learning more about the SafeGuard Cyber solution, you can take a quick 5-minute tour.
