LinkedIn social engineering scams continue to increase, and even cybersecurity professionals like me are not exempt from such encounters. And even though this particular attempt evoked more of an eye roll, I believe it’s still worth sharing for two reasons:
- LinkedIn phishing and social engineering scams are real and costly. How costly? To give just one example, scammers on LinkedIn cost Axie Infinity more than half a billion dollars with a fake job offer.
- When weaponized by social engineers, LinkedIn is an extremely potent and effective vector because it preys upon one’s self-worth and identity. Phishing in social media can be greatly damaging, especially to new users and individuals trying to find work or enter any field.
So, without further ado, this is the anatomy of a LinkedIn social engineering scam that targeted me.
Dangling the Bait
It started innocently enough; in a message, the scammer mentioned ‘podcast,’ meaning to lure me as a podcast host.
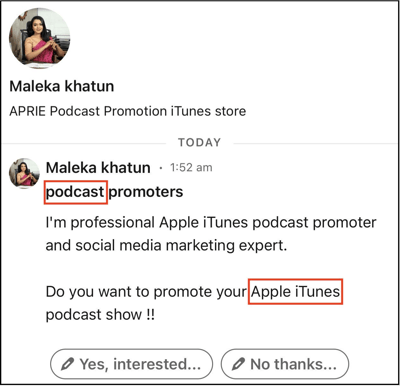
However, given the rudimentary nature of the message and non-native syntax, it became immediately obvious that the scammers most likely did their reconnaissance by scraping profile data. Particularly, their outreach message is generic and could be directed at anyone with ‘podcast’ in their title.
But this podcast scam had another ace: the appeal to ego. This tactic makes sense: who doesn’t want someone promoting them, right? More effective attacks, particularly job scams, are tailored to targets’ interests, skill sets, and professional aspirations. They mention a specific ‘episode’ of your career. For example, they’ll bring up the possibility of promotion from director to VP. They’ll follow that up with specific skill sets evident on other LinkedIn profiles.
Again, this may sound easy to detect and deflect, but Linkedin social engineering attacks are exactly how threat actors like the Lazarus Group, OilRig, and Chinese counterintelligence have successfully compromised employees in defense, aerospace, cybersecurity, and network administration. After connecting, threat groups will either move the conversation to another channel like WhatsApp, or simply pass a document like a job description or keynote speaker application to the target. From there, a payload is delivered to gain access to systems or intellectual property.
Sniffing Out the Fraud
There are ways to sniff out scammers on LinkedIn, even when the message is targeted and more tailored:
- Look at their posts (or lack thereof). In this example, the scammer is a purported ‘social media expert.’ However, their profile was barren and not a post in sight.
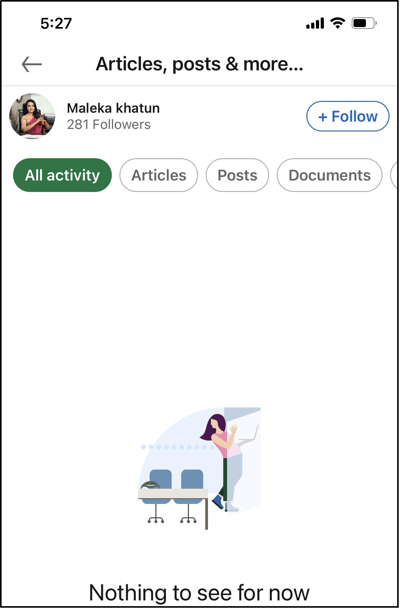
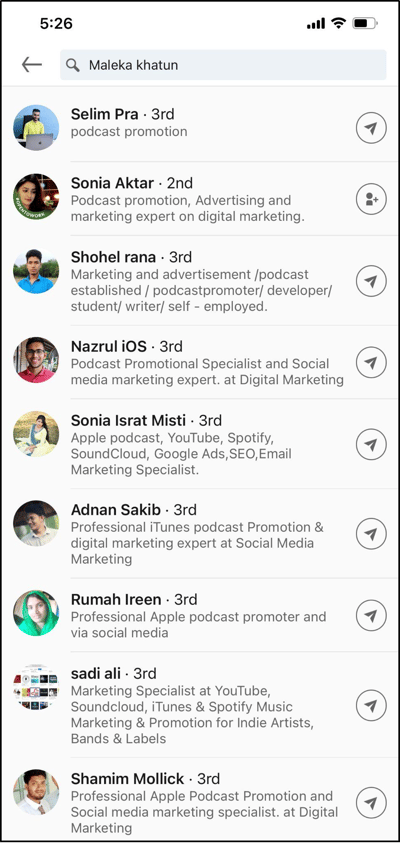
Side note: There are also instances where scammers do have posts in their profile, but they often do not sound like experts at all. Sure, not every post is perfect, and grammar should be the least of your worries on your LinkedIn post. But when the supposedly expert insight on the topic does not make sense at all or is not backed by facts and data, you might be looking at a scammer’s profile. - Clicking through the profile reveals a ton more accounts connected to one another with the same uninspired bios and job descriptions.
- Linkedin social engineering profiles often look professional. However, a quick reverse image search shows the picture is a common stock photo used somewhere around the world (in my case, it was in Bangladesh).

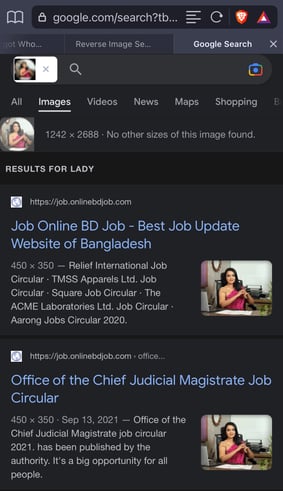
An important note, however: image search is not a failsafe, especially when it’s become really easy to generate ‘fake’ people through AI-generated profile pictures (see This Person Does Not Exist as a reference). - Typically after viewing their profile, you immediately get a notification that they’re ‘following’ you, which is another attempt to appeal to your ego.
A Futile but Eye-Opening Attempt
Long story short, I blocked this account and reported the profile as LinkedIn phishing. As a cybersecurity professional, it’s funny thinking about the futility of the attempt. This was most likely a small-time phishing organization, with the way their profile and their messaging were set up.
Still, the experience is eye-opening all the same, because even poorly-written LinkedIn social engineering scams can snag unsuspecting people. Job seekers who are new to LinkedIn or others not savvy with security are particularly susceptible.
We as cybersecurity veterans should spread the word and take the time to educate any non-industry people around us. Social engineering leaves scars, sometimes across the data in your network, sometimes in your bank account. But it also leaves a much deeper scar on a victim’s sense of trust in people.
Don’t let these scammers take that from anyone you know.
(Read the original LinkedIn post here.)
If you are interested in learning more about the SafeGuard Cyber solution, you can take a quick 5-minute tour.
