WHITEPAPER
Paradigm Shift: Agentless Security
How to protect your company’s data and
your hybrid workforce at scale.
Begin your transformation to secure and compliant communication. Share your information so we can connect.

Download PDF
Executive Summary
The receding pandemic has left behind a paradigm shift in the work environment, one that is built around the cloud. Even as workers return to the office, many companies are planning to proceed with a hybrid model that includes some remote work. Realizing that workplace flexibility increases worker engagement and productivity, organizations are adapting to a new workplace.
The change in the way we work means we will need to change the way we secure our systems. Traditional agent-based security solutions will be insufficient. As the attack surface of hybrid work grows more complex, security teams need solutions that reduce complexity and deploy quickly.
This whitepaper describes the challenges of threat detection and response for cloud-based collaboration and communications solutions. It also details how a new agentless security model ensures better performance for security teams by reducing mean time to detection and response (MTTD/R). With this new model, organizations benefit from rapid, scalable deployment, gain time to value, eliminate the need to manage agents, and gain better protection for business-critical cloud communication environments, on any network or device.
The Changing Nature of Work
The pandemic accelerated this shift to work from home (WFH). During the pandemic, 97% of North American office workers worked from home more than one day per week whereas 67% had not worked remotely prior to COVID-19. It’s unlikely that these workers will ever come back to full time in the office.
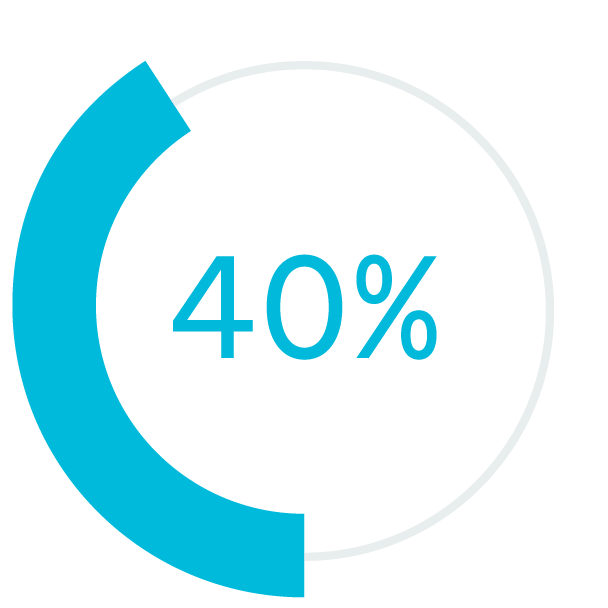
Going forward, most organizations will likely employ a mix of in-office and remote work both to accommodate worker preference and to achieve significant benefits for the organization. More than 80% of workers prefer a hybrid work environment. Moreover, research shows that flexible work arrangements increase engagement. When employees are engaged, performance soars: Highly engaged workplaces claim 41% lower absenteeism, 40% fewer quality defects, and 21% higher profitability.
of North American office workers worked from home more than one day per week
had not worked remotely prior to COVID-19
of workers prefer a hybrid work environment
The Changing Nature of Work
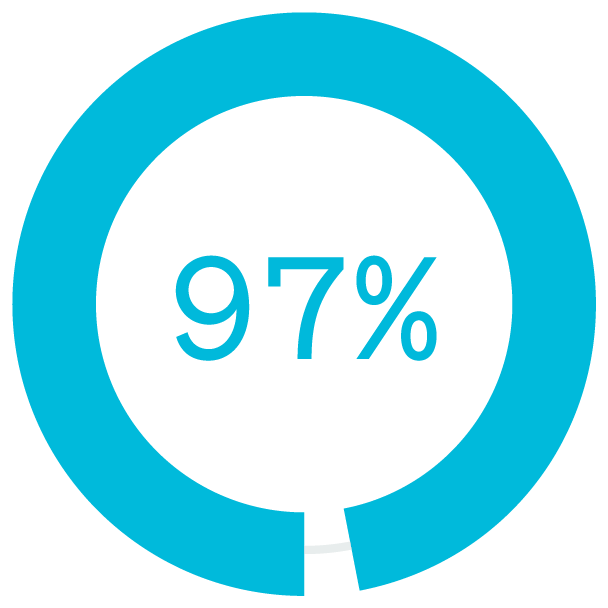
of North American office workers worked from home more than one day per week
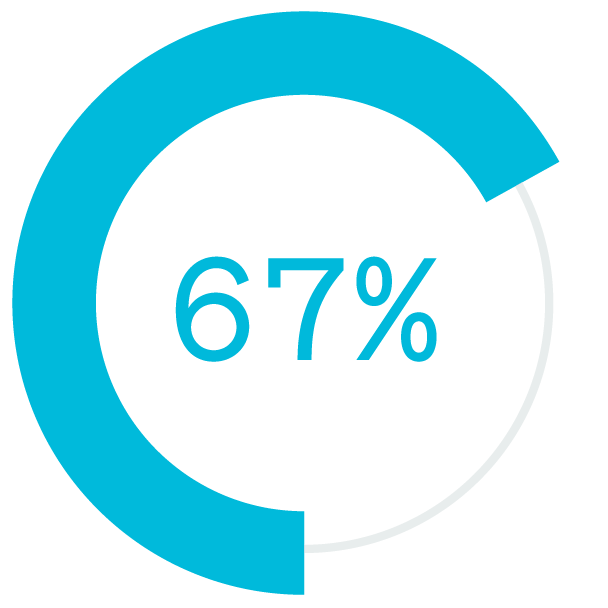
had not worked remotely prior to COVID-19
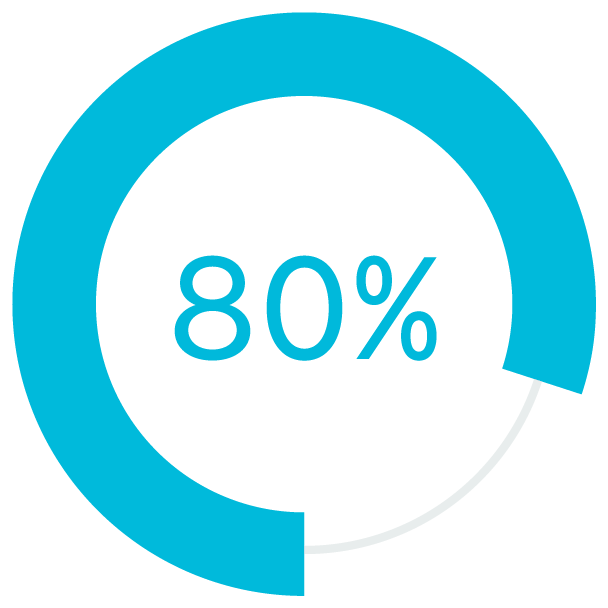
of workers prefer a hybrid work environment
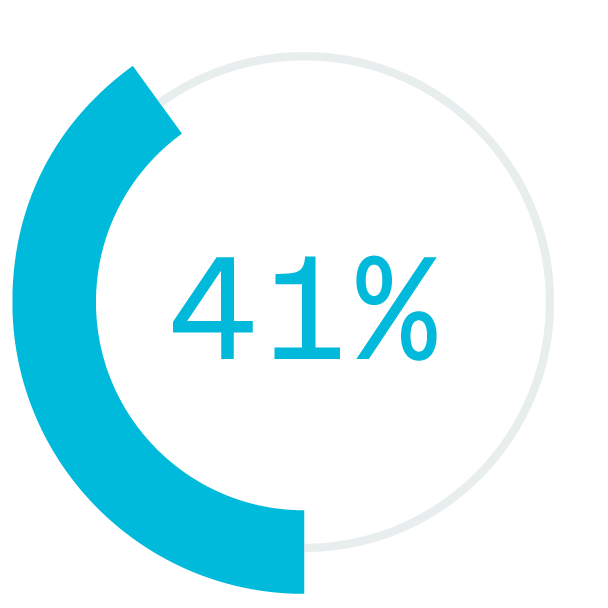
lower absenteeism
fewer quality defect
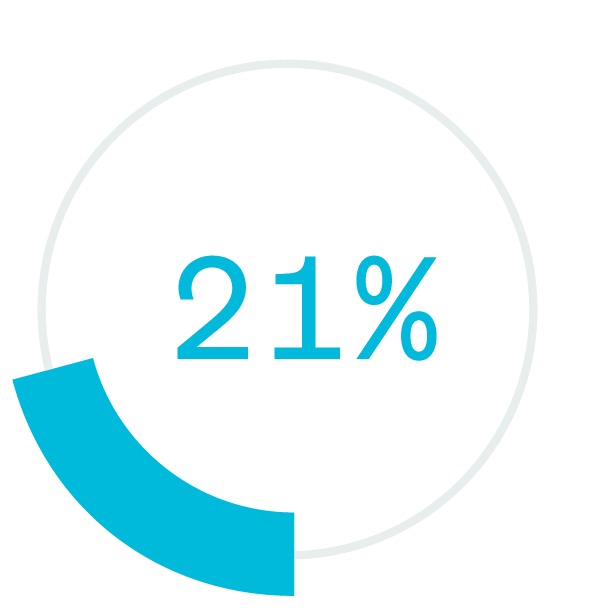
higher profitability
Something Powerful
Tell The Reader More
The headline and subheader tells us what you're offering, and the form header closes the deal. Over here you can explain why your offer is so great it's worth filling out a form for.
Remember:
- Bullets are great
- For spelling out benefits and
- Turning visitors into leads.
lower absenteeism
fewer quality defect
higher profitability
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements for Flexible Work Environments
As organizations rely on cloud apps to enable hybrid work, they must also look to secure business data against the risks that come with these applications. The most prevalent cloud communication apps lack sufficient visibility or security controls.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
NEW ROLE OF THE CISO
Over 80% of security professionals believe social media, mobile messaging, or collaboration apps present medium to high risks to their organization.
SafeGuardCyber Survey April, 2019
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Text
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.

Collaboration and Communications Applications
Organizations also increasingly rely on cloud-based collaboration platforms and personal communications technologies to connect teams across regions and time zones.
Now, more than a year later, not only are organizations continuing to use these technologies, but they’re doubling down. Yet, they still have no way to keep these systems secure from third-party risks. For example, a recent attack against EA Games involved infiltrating the company’s Slack instance and launching a fileless social engineering scheme to gain access to the network, resulting in the theft and exfiltration of highly-valuable intellectual property.
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Organizations also increasingly rely on cloud-based collaboration platforms and personal communications technologies to connect teams across regions and time zones.
With the sudden onset of the pandemic, many organizations abruptly switched to remote work and found themselves having to allow technologies like MS Teams, Slack, Zoom and Webex on a scale they were uncomfortable permitting earlier. At the time, many IT leaders believed these solutions would be temporary and they’d quickly go back to "normal."
Now, more than a year later, not only are organizations continuing to use these technologies, but they’re doubling down. Yet, they still have no way to keep these systems secure from third-party risks. For example, a recent attack against EA Games involved infiltrating the company’s Slack instance and launching a fileless social engineering scheme to gain access to the network, resulting in the theft and exfiltration of highly-valuable intellectual property.
Similarly, IT once viewed communications solutions like WhatsApp and WeChat as personal apps. Because corporate teams had zero visibility into them, they would not allow employees to do business on them. But in some critical emerging markets, only a small percentage of people use email. Most use mobile chat applications like WhatsApp. It has become a business imperative to use the local technology.
New Security Challenges
These collaboration and communications tools present significant data governance and security challenges for large organizations. In a survey by SafeGuard Cyber:
- 78% of cybersecurity leaders express an inability to protect all communication channels and digital assets6
- 46% say collaboration tools represent the biggest security challenge
- 1 in 3 say their biggest challenge is mobile chat apps, WhatsApp, WeChat, Telegram
- 1 in 5 say their biggest challenge is Video meetings (Zoom, Webex, etc. )
Hybrid work environments will only increase the challenges. As employee devices and laptops move onto the corporate network and then back home where they can be exposed to hackers and more easily infected with malware and ransomware, it will be difficult for security teams to protect employees from threats, detect and respond to insider threats, or stop malware and ransomware.

Only 20% of security professionals feel confident they are effectively mitigating the digital risks from social media, messaging and collaboration apps.
SafeGuardCyber Survey April, 2019
New Security Challenges
These collaboration and communications tools present significant data governance and security challenges for large organizations. In a survey conducted by SafeGuard Cyber:
- 78% of cybersecurity leaders express an inability to protect all communication channels and digital assets
- 46% say collaboration tools represent the biggest security challenge
- 1 in 3 say their biggest challenge is mobile chat apps, WhatsApp, Telegram.
- 1 in 5 say their biggest challenge is Video meetings (Zoom, Webex, etc. )
Hybrid work environments will only increase the challenges. As employee devices and laptops move onto the corporate network and then back home where they can be exposed to hackers and more easily infected with malware and ransomware, it will be difficult for security teams to protect employees from threats, detect and respond to insider threats, or stop malware and ransomware.
Agent-Based Security Solutions Are Ineffective for the Hybrid Workforce
Companies need to deliver secure communications for both BYOD and enterprise devices on a continual and consistent basis. Unfortunately, as organizations move to hybrid remote/on-premises working arrangements, old ways of securing systems and devices no longer suffice.
Traditional agent-based solutions presented two challenges:
- When installed on machines across a network, these solutions drag down overall network performance.
- Managing these solutions adds unnecessary complexity to security team’s daily workloads. Security teams must manage dozens of configurations for thousands of devices, with no visibility on BYOD machines.
Changes in the infrastructure to accommodate hybrid work environments make it even more onerous and less effective to deploy agent-based software.

SafeGuardCyber Survey April, 2019
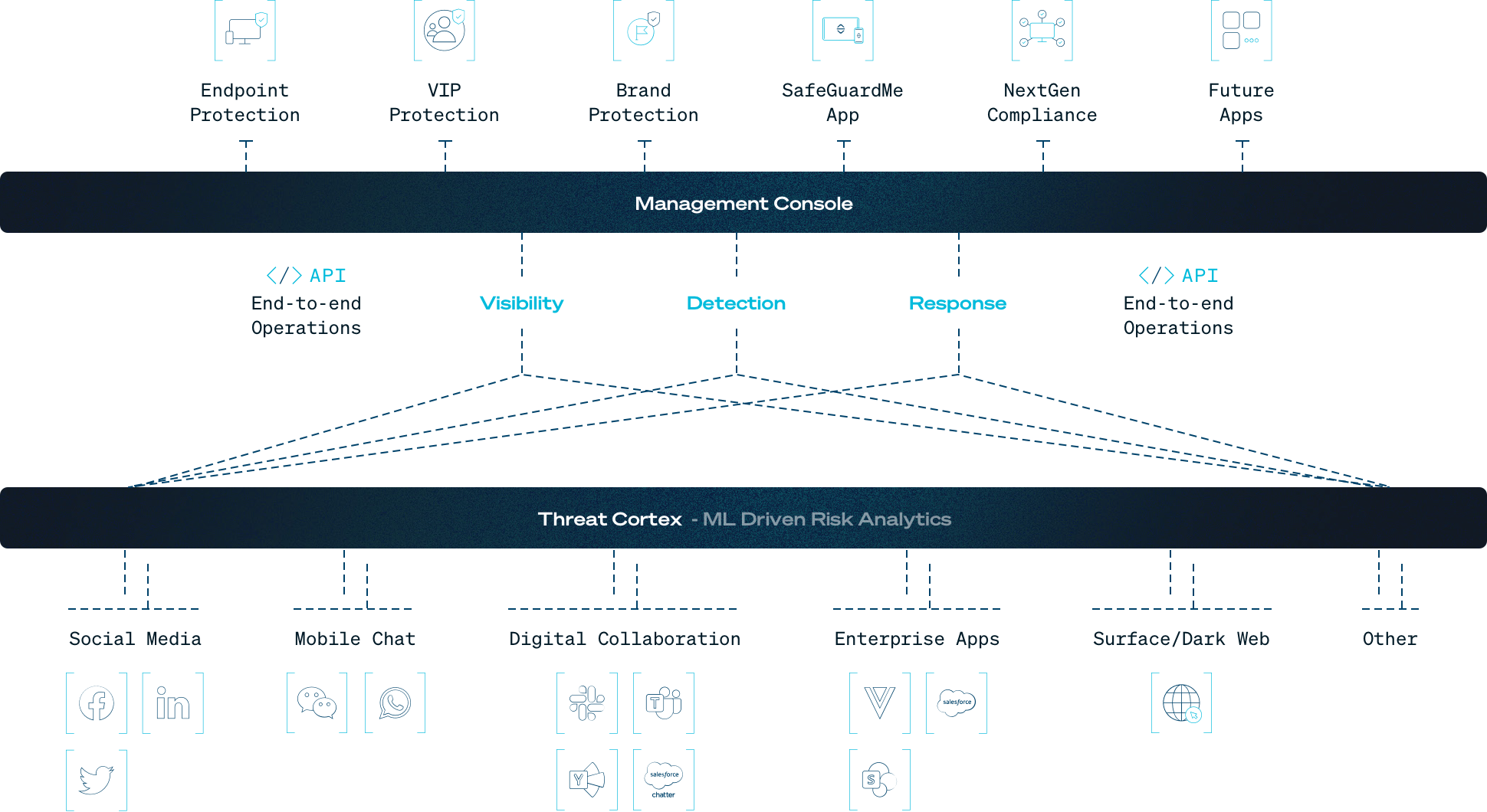
The SafeGuard Cyber Solution
SafeGuard Cyber delivers a human-centric security solution purpose-built on an agentless architecture in the cloud. The solution authenticates directly into cloud communication and collaboration platforms. No agent configuration. Authorization at the administrator level ensures a portable security layer is extended to any instance, with visibility to detect and respond to internal and external threats at the message level.
The unique benefits of SafeGuard Cyber’s agentless architecture include immediate time-to-value, reduced cost and complexity, and better protection for business-critical cloud communication environments. With streamlined deployment, SafeGuard Cyber delivers a portable security layer that is device and network agnostic. Employees are free to access the cloud applications they need to work effectively, on mobile or desktop apps or even via browsers, and the security controls remain intact. Stop attacks in the cloud before they reach physical endpoints.
SafeGuardCyber Survey April, 2019
Today’s attackers don’t come in through a single door. They might groom a target on social media, send a DM or email, or even attack without even using a file. Agentless security provides holistic security across the entire system. Because SafeGuard Cyber can apply controls at the message level, teams have one platform to detect and respond to data loss, insider threats, and malicious content. Organizations no longer need separate DLP, malware detection, and so on.

SafeGuardCyber Survey April, 2019
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla urna massa, maximus at neque vel, mollis efficitur.
With SafeGuard Cyber’s agentless architecture, organizations benefit from:
Faster MTTD/R
Gain unprecedented visibility to respond to internal and external threats in hard-to-see places like direct messages and group channels.
Rapid Time to Value
Be up and running in hours not days. Organizations no longer have to configure agents.
Integrated Defense
Connect our agentless security platform into your existing cyber defense systems, feeding event data and telemetry into your EDR and SIEM solutions.
Benefits
With SafeGuard Cyber’s agentless architecture, organizations benefit from:
Gain unprecedented visibility to respond to internal and external threats in hard-to-see places like direct messages and group channels. Reduce detection and response times in the cloud infrastructure where work gets done.
Be up and running in hours not days. Organizations no longer have to configure agents.
Connect our agentless security platform into your existing cyber defense systems, feeding event data and telemetry into your EDR and SIEM solutions.
Conclusion
With SafeGuard Cyber, organizations can now rest assured that no matter where their employees are working—whether at the office, on the road, or at home—communication and collaboration apps running on any device or network will be protected. Moreover, they can deploy this protection rapidly.

Secure Human Connections
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest insider threats, ransomware, and third-party vulnerabilities.



