Q+A FEATURING
Joseph Blankenship | Security & Risk VP Research Director, Forrester
From Lapsus$ to 0ktapus, devastating recent breaches have used low-cost social engineering attacks across multiple channels, targeting employees across LinkedIn, WhatsApp, email, Slack, and more.
After two decades, it’s time to move beyond just awareness training. Security teams need technical controls to detect and stop this persistent threat. In this Q&A with guest speaker Forrester’s Joe Blankenship, we continue the conversation from our Expert Panel discussion, “Beyond Training: Technical Controls to Stop Social Engineering.”
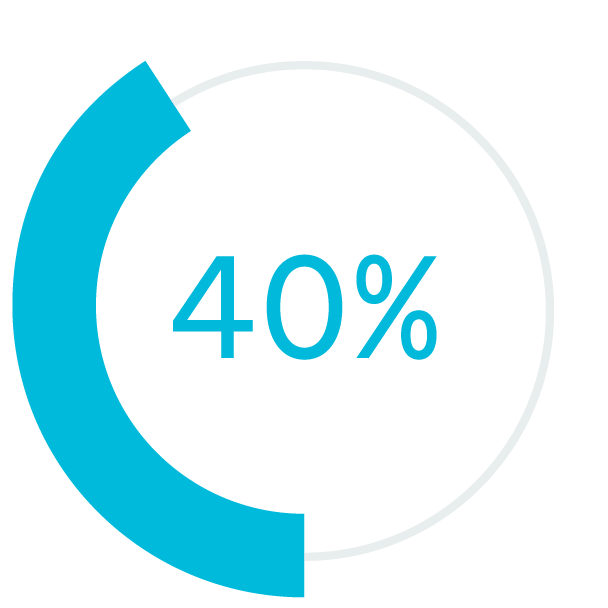
of business communication is now in digital channels outside of email1
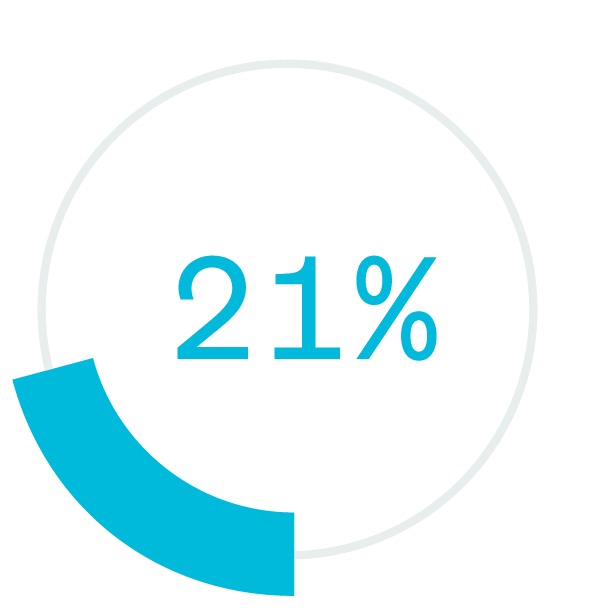
of breaches in the last year involved an element to exploit a human vulnerability2
of social engineering attacks achieve infiltration3
Business Communications Report 2022; Verizon, 2022 Data Breach Investigations Report; Verizon, 2021 Data Breach Investigations Report
The Changing Nature of Work
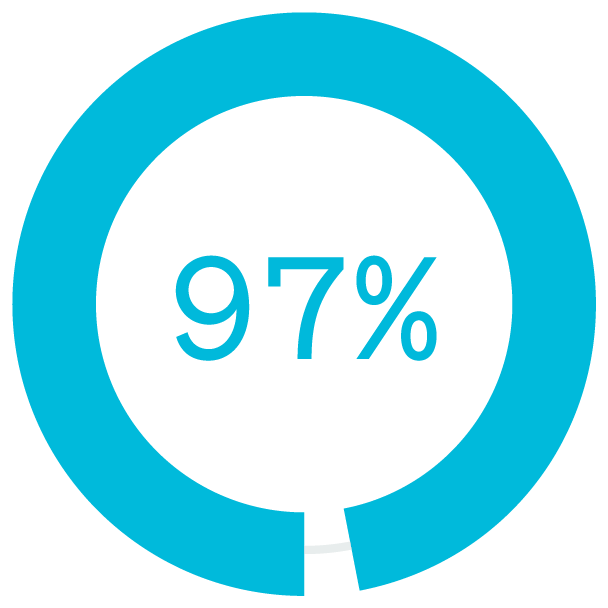
of North American office workers worked from home more than one day per week
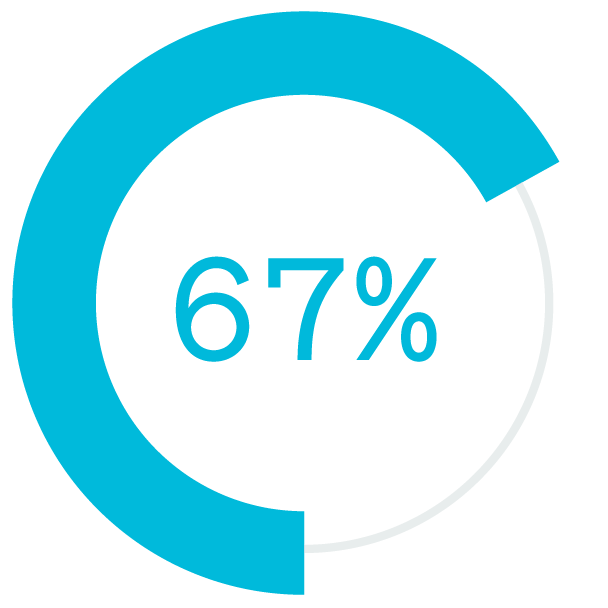
had not worked remotely prior to COVID-19
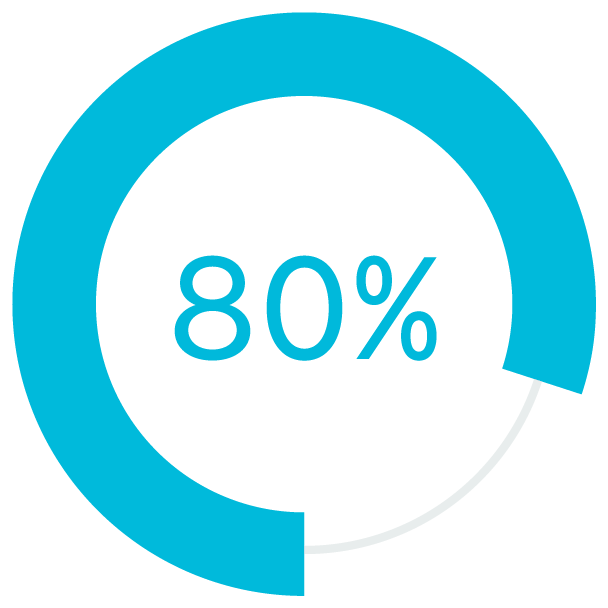
of workers prefer a hybrid work environment
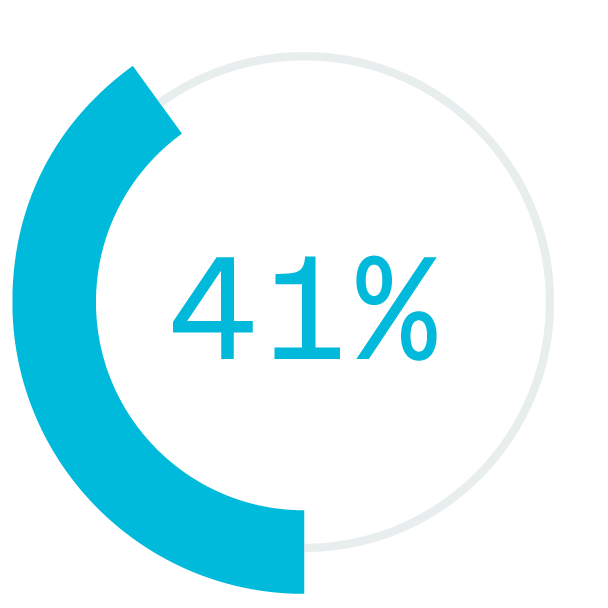
lower absenteeism
fewer quality defect
higher profitability
Something Powerful
Tell The Reader More
The headline and subheader tells us what you're offering, and the form header closes the deal. Over here you can explain why your offer is so great it's worth filling out a form for.
Remember:
- Bullets are great
- For spelling out benefits and
- Turning visitors into leads.
lower absenteeism
fewer quality defect
higher profitability
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
NEW ROLE OF THE CISO
Over 80% of security professionals believe social media, mobile messaging, or collaboration apps present medium to high risks to their organization.
SafeGuardCyber Survey April, 2019
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Organizations also increasingly rely on cloud-based collaboration platforms and personal communications technologies to connect teams across regions and time zones.
With the sudden onset of the pandemic, many organizations abruptly switched to remote work and found themselves having to allow technologies like MS Teams, Slack, Zoom and Webex on a scale they were uncomfortable permitting earlier. At the time, many IT leaders believed these solutions would be temporary and they’d quickly go back to "normal."
Now, more than a year later, not only are organizations continuing to use these technologies, but they’re doubling down. Yet, they still have no way to keep these systems secure from third-party risks. For example, a recent attack against EA Games involved infiltrating the company’s Slack instance and launching a fileless social engineering scheme to gain access to the network, resulting in the theft and exfiltration of highly-valuable intellectual property.
Similarly, IT once viewed communications solutions like WhatsApp and WeChat as personal apps. Because corporate teams had zero visibility into them, they would not allow employees to do business on them. But in some critical emerging markets, only a small percentage of people use email. Most use mobile chat applications like WhatsApp. It has become a business imperative to use the local technology.
New Security Challenges
These collaboration and communications tools present significant data governance and security challenges for large organizations. In a survey by SafeGuard Cyber:
- 78% of cybersecurity leaders express an inability to protect all communication channels and digital assets6
- 46% say collaboration tools represent the biggest security challenge
- 1 in 3 say their biggest challenge is mobile chat apps, WhatsApp, WeChat, Telegram
- 1 in 5 say their biggest challenge is Video meetings (Zoom, Webex, etc. )
Hybrid work environments will only increase the challenges. As employee devices and laptops move onto the corporate network and then back home where they can be exposed to hackers and more easily infected with malware and ransomware, it will be difficult for security teams to protect employees from threats, detect and respond to insider threats, or stop malware and ransomware.

Joseph Blankenship
VP, Research Director

SGC Q: Work from anywhere is here to stay. How enterprise employees communicate has evolved to using a variety of cloud communication channels to get the job done. How do cloud collaboration, social media, and mobile messaging applications impact the way security teams protect enterprise data and people?
JB A: Users are bombarded with messages and requests daily, and it’s easy for them to become distracted or make the wrong decision in the moment. It’s not sufficient to leave data security to users. They need security controls that protect them from accidentally sharing data outside of policy or responding to social engineering techniques. Security teams have not widely deployed controls for collaboration, messaging, and social media like they have for enterprise applications like email. Protection has to evolve to include other means of communication and data sharing to reduce risk.

SGC Q: Attacker techniques and tactics are becoming more sophisticated even as workforce employees share more personal and enterprise information on channels like LinkedIn and WhatsApp. What’s the risk versus reward of the security team enabling more modern business communication channels?
JB A: Work From Anywhere increased dependence on messaging and collaboration tools – with internal and external users. While this does empower our ability to communicate more effectively in real time (since we can’t pop over to someone’s desk anymore), it did introduce risk. Users share all kind of sensitive data in these tools – intellectual property, PII, PHI, and sensitive internal correspondence. Opening collaboration tools up externally introduces all the risks we already experience with email – phishing, accidental data loss, and account compromise. This means we have to balance the benefit of real-time communication with contractors, vendors, and partners who may be external to the organization with the risk that the collaboration and communication tools may be misused. If users inherently trust the tool, they become more susceptible to attacks like social engineering since they aren’t necessarily looking out for attackers or malicious behavior in those channels.


SGC Q: Lapsus$ stealing source code, Twilio compromised, Axie Infinity robbed of half a billion dollars. It wasn’t zero days or custom exploits. So many headline-making breaches in 2022 came down to social engineering employees. Can you comment on this trend and provide insight into how security teams can and should calibrate their strategies to mitigate these risks?
JB A: Social engineering is arguably the oldest hacking technique. It predates the internet and even computers. What’s changed is that the connectivity made it easier for attackers to reach a wider number of victims, and the victims rarely ever meet the attackers in the real world. Social engineering works because it preys on users’ emotions and desire to be helpful. Attackers, just like old-school conmen, gain their victims’ trust or bully them into taking an action without carefully considering it. Security strategies have to evolve so that they don’t rely only on the user making the right decision in the moment. They need to include real-time education and the ability to stop users from taking risky actions.

SGC Q: Is security training enough to combat social engineering? If not, how does it need to evolve, and what is the correct balance between controls and security awareness training to defend against social engineering?
JB A: Awareness of social engineering and social engineering techniques alone has not proven effective. Users may forget what they’ve learned or think that the person targeting them is trustworthy. That means security teams have to design interventions that keep users from giving up sensitive information (especially account credentials), clicking on links, or downloading files. Those controls have to work in the moment to stop users from falling victim to attacks. At the same time, the controls can’t introduce so much friction as to constantly interrupt work or encourage users to circumvent the controls. Controls should be risk-based, so they are only disrupting users that exhibit risky behaviors and are taking risky actions.

SafeGuardCyber Survey April, 2019
SafeGuardCyber Survey April, 2019
SafeGuardCyber Survey April, 2019
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla urna massa, maximus at neque vel, mollis efficitur.
Benefits
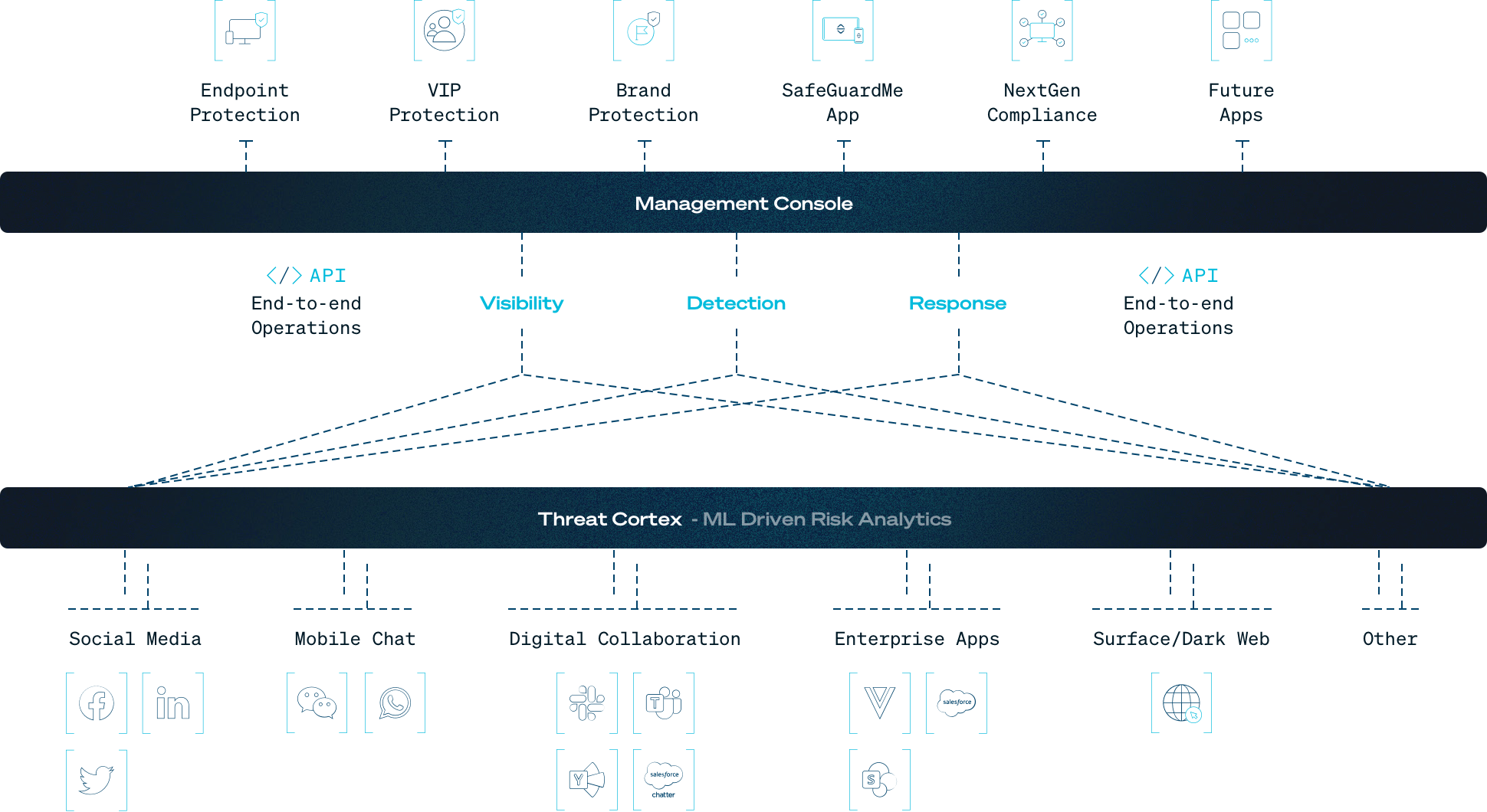
With SafeGuard Cyber’s agentless architecture, organizations benefit from:
Gain unprecedented visibility to respond to internal and external threats in hard-to-see places like direct messages and group channels. Reduce detection and response times in the cloud infrastructure where work gets done.
Be up and running in hours not days. Organizations no longer have to configure agents.
Connect our agentless security platform into your existing cyber defense systems, feeding event data and telemetry into your EDR and SIEM solutions.
SafeGuard Cyber is the most comprehensive integrated cloud communications security platform to address cybersecurity threats and compliance risks across today’s modern cloud workplace. Through a combination of unified visibility, contextual analysis, and multi-channel investigations and detections, SafeGuard Cyber mitigates risks in email, mobile and web messaging apps, collaboration apps, and social media.
Powered by Natural Language Understanding (NLU) and patented Social Engineering Detection technologies, the SafeGuard Cyber platform reduces investigation and detection hours to minutes while providing resolution of social engineering and language-based attacks in over 50 languages.

Secure Human Connections
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest insider threats, ransomware, and third-party vulnerabilities.


