WHITEPAPER
Stopping Social Engineering Attacks with Natural Language Understanding for Early Detection and Response
Companies spend millions of dollars on tools to protect their data and systems from cloud workspace vulnerabilities. But a convincing chat or an urgent-looking message can help a threat actor to easily bypass all of these security protocols.
Begin your transformation to secure and compliant communication. Share your information so we can connect.

Download PDF
Introduction
Companies spend millions on tools to protect their data and systems from cloud workspace vulnerabilities. But a convincing chat or an urgent-looking message can help a threat actor to easily bypass all of these security protocols. Consider the EA Games breach in 2021: one Slack session cookie purchased for $10 on the dark web allowed hackers to gain access to their systems, resulting in a 780GB data theft. Threat actors know all this. SafeGuard Cyber’s FirstSight platform, with its advanced threat detection capabilities, including Contextual AI, addresses these vulnerabilities by providing comprehensive visibility and rapid remediation in such scenarios.
Security teams urgently need to protect and secure employees from social engineering attacks across social media and within enterprise collaboration applications. They need comprehensive visibility into business communications for threat detection and response.
This advanced threat detection capability should also enable quarantine and remediation of malicious files and links. It should also be capable of detecting the patterns, context, and intent of communications that indicate the early stages of phishing, social engineering, and business communication compromise attacks.
The Threat in Numbers
Threat actors are increasingly taking aim at the cloud workspace to conduct social engineering. They are financially motivated and gather intelligence from social networks to specifically target key employees and executives.
average cost for data breaches initiated through social engineering techniques
of all cyber-attacks accounts for social engineering
of total breaches involved the human element, highlighting the persistent vulnerability of human factors in cybersecurity
Social engineering
n., an attack vector that heavily relies on human interaction (often involves manipulating people into breaking normal security procedures and best practices) for financial gain and/or unauthorized access to systems, networks, or physical locations.
---
The Changing Nature of Work
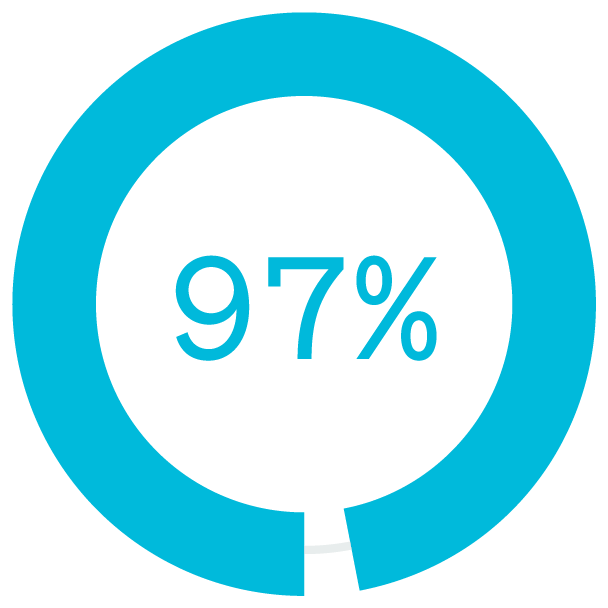
of North American office workers worked from home more than one day per week
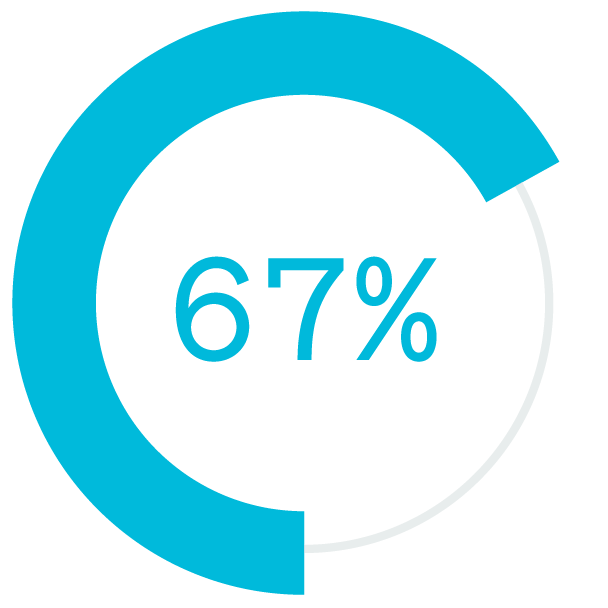
had not worked remotely prior to COVID-19
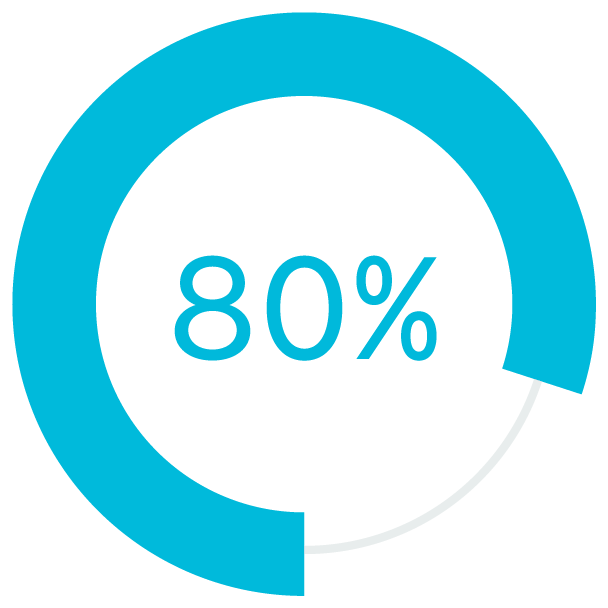
of workers prefer a hybrid work environment
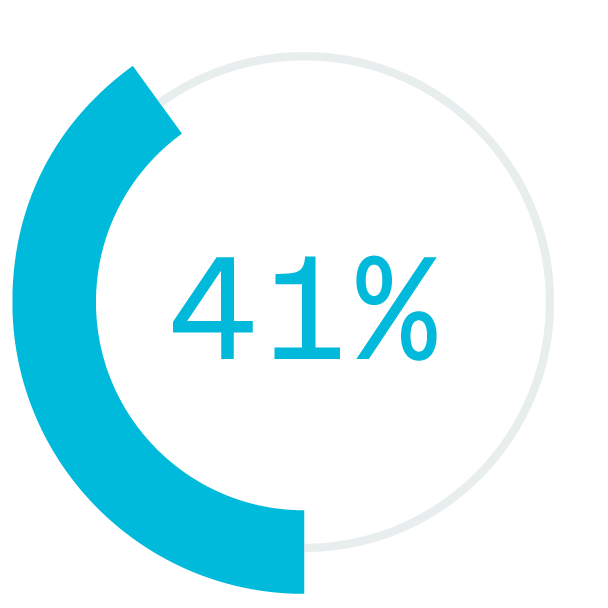
lower absenteeism
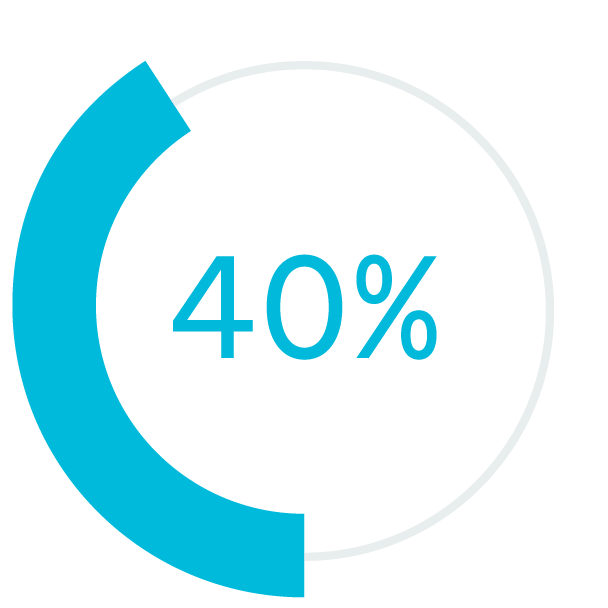
fewer quality defect
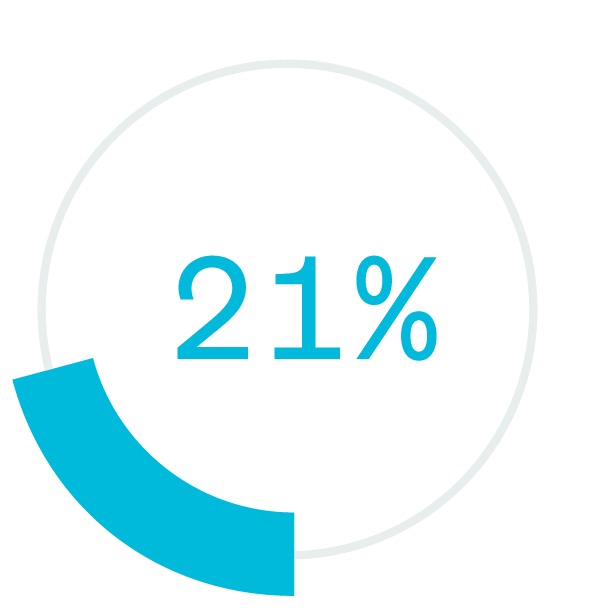
higher profitability
Something Powerful
Tell The Reader More
The headline and subheader tells us what you're offering, and the form header closes the deal. Over here you can explain why your offer is so great it's worth filling out a form for.
Remember:
- Bullets are great
- For spelling out benefits and
- Turning visitors into leads.
lower absenteeism
fewer quality defect
higher profitability
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Technical Requirements
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
NEW ROLE OF THE CISO
Over 80% of security professionals believe social media, mobile messaging, or collaboration apps present medium to high risks to their organization.
SafeGuardCyber Survey April, 2019
Secure Infrastructures
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Text
Flexible work environments require access to on-premises systems and data, and therefore most enterprises rely on employees using a VPN. However, organizations can’t trust that workers will always use these secure channels. If an employee is using a mobile phone, he or she might forget to use the VPN and employ an unsecured wireless network instead, exposing corporate systems and data to risk.
During the pandemic, threat actors realized that insecure home networks and a lack of security controls typically found on corporate networks could work to their benefit. The World Economic Forum estimates cyber attacks jumped 238% globally between February and April 2020.
Organizations also increasingly rely on cloud-based collaboration platforms and personal communications technologies to connect teams across regions and time zones.
With the sudden onset of the pandemic, many organizations abruptly switched to remote work and found themselves having to allow technologies like MS Teams, Slack, Zoom and Webex on a scale they were uncomfortable permitting earlier. At the time, many IT leaders believed these solutions would be temporary and they’d quickly go back to "normal."
Now, more than a year later, not only are organizations continuing to use these technologies, but they’re doubling down. Yet, they still have no way to keep these systems secure from third-party risks. For example, a recent attack against EA Games involved infiltrating the company’s Slack instance and launching a fileless social engineering scheme to gain access to the network, resulting in the theft and exfiltration of highly-valuable intellectual property.
Similarly, IT once viewed communications solutions like WhatsApp and WeChat as personal apps. Because corporate teams had zero visibility into them, they would not allow employees to do business on them. But in some critical emerging markets, only a small percentage of people use email. Most use mobile chat applications like WhatsApp. It has become a business imperative to use the local technology.
New Security Challenges
These collaboration and communications tools present significant data governance and security challenges for large organizations. In a survey by SafeGuard Cyber:
- 78% of cybersecurity leaders express an inability to protect all communication channels and digital assets6
- 46% say collaboration tools represent the biggest security challenge
- 1 in 3 say their biggest challenge is mobile chat apps, WhatsApp, WeChat, Telegram
- 1 in 5 say their biggest challenge is Video meetings (Zoom, Webex, etc. )
Hybrid work environments will only increase the challenges. As employee devices and laptops move onto the corporate network and then back home where they can be exposed to hackers and more easily infected with malware and ransomware, it will be difficult for security teams to protect employees from threats, detect and respond to insider threats, or stop malware and ransomware.

Only 20% of security professionals feel confident they are effectively mitigating the digital risks from social media, messaging and collaboration apps.
SafeGuardCyber Survey April, 2019
How Social Engineers Hack the Brain
Scammers and social engineers successfully “hack” the brain of their victims because they often use human emotional responses to trigger action. Jenny Radcliffe, also known as The People Hacker, witnessed in her 30 years of cybersecurity experience how social engineering evolved – from long cons and frauds in pubs or cafes to social media stalking.
In her speech during Infosecurity Europe 2022, Jenny reminds the cybersecurity community that criminals will always focus on human weakness, despite the growth of technology.

“We can’t defend without working closely together. I’ve had tech companies and directors dismiss social engineering as about phishing, or sneaking past with a wink and a smile. It’s never that easy...the answer to good security has always been with the people.”
— Jenny Radcliffe, The People Hacker
On one occasion, a security company that simulated phishing emails yielded worrisome results:
- The phishing email promised victims they’d ‘win’ a new iPhone if they clicked on the link provided and entered their domain credentials. Out of 1000 people who received the phishing email, 75% complied.
- As a follow-up to the first test, another simulation was launched with the would-be attacker posing as someone from tech support. The attacker informs the top 25 of those who complied with the first test that their device was infected with malware. To ‘clean’ it, they were told to download an app, which was actually a reverse shell allowing access to their desktops. 24 out of 25 obeyed.
Social engineering, when performed with such insight into human behavior, can have terrifying results and consequences.

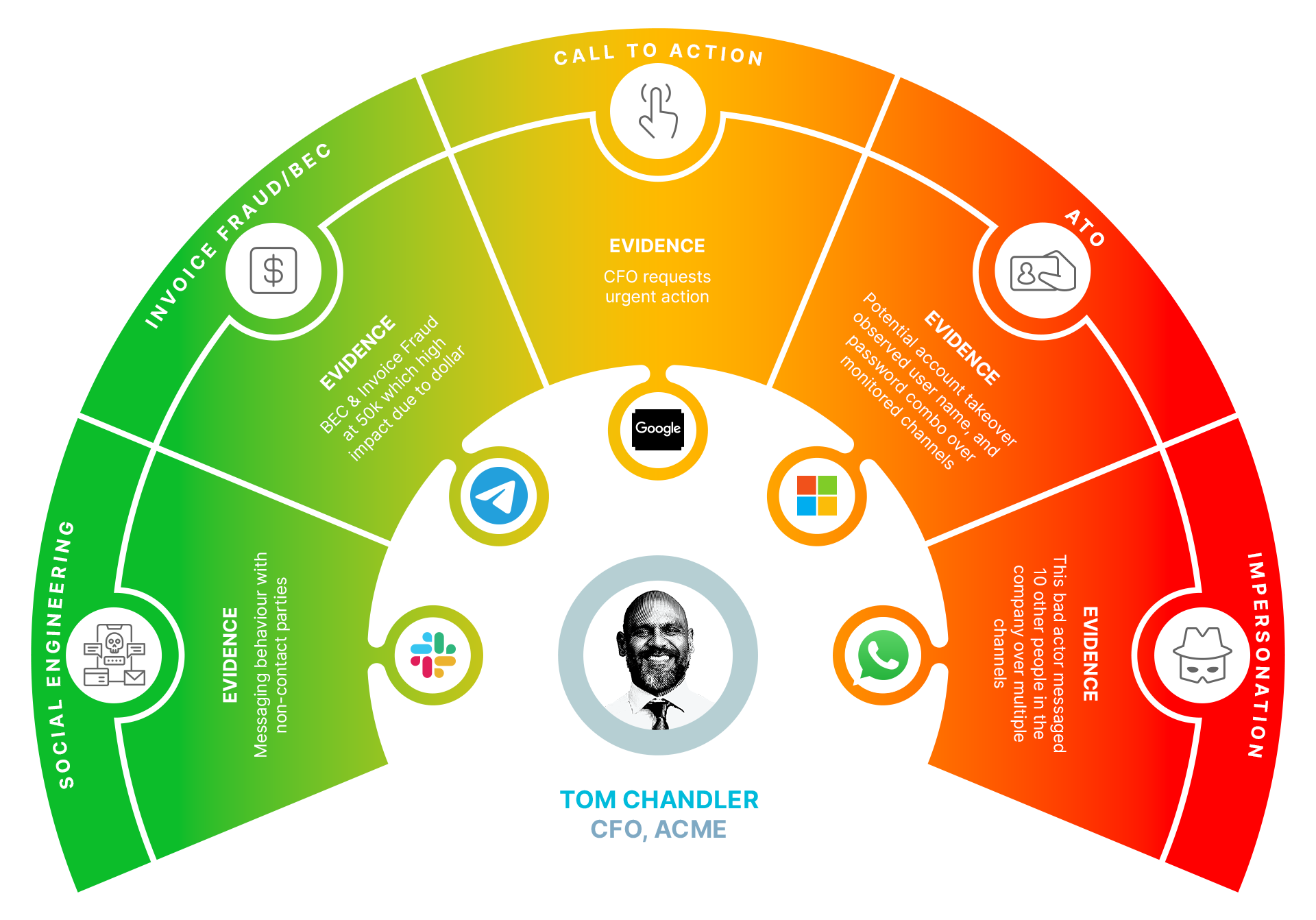
Anatomy of a Social Engineering Attack
Social engineering threats typically involve attackers using fake accounts to communicate with targets, posing as legitimate business contacts or recruiters.
Social engineering messages may not include malicious payloads such as files or links. This makes them difficult to detect with traditional security tools like endpoint and secure email gateways. Instead of a payload, the attacker attempts to entice a recipient to take an action or divulge private or sensitive information. The business consequences include credential theft, data loss, account takeover, blackmail, payroll fraud, and vendor invoice fraud.
SafeGuardCyber Survey April, 2019
How Can Security Teams Truly Protect Their Organizations?
Determined threat actors can circumvent the basic protections listed above.
Some protective steps can deter bots and automated attacks, but traditional systems don’t stand a chance against experienced phishers and hackers.
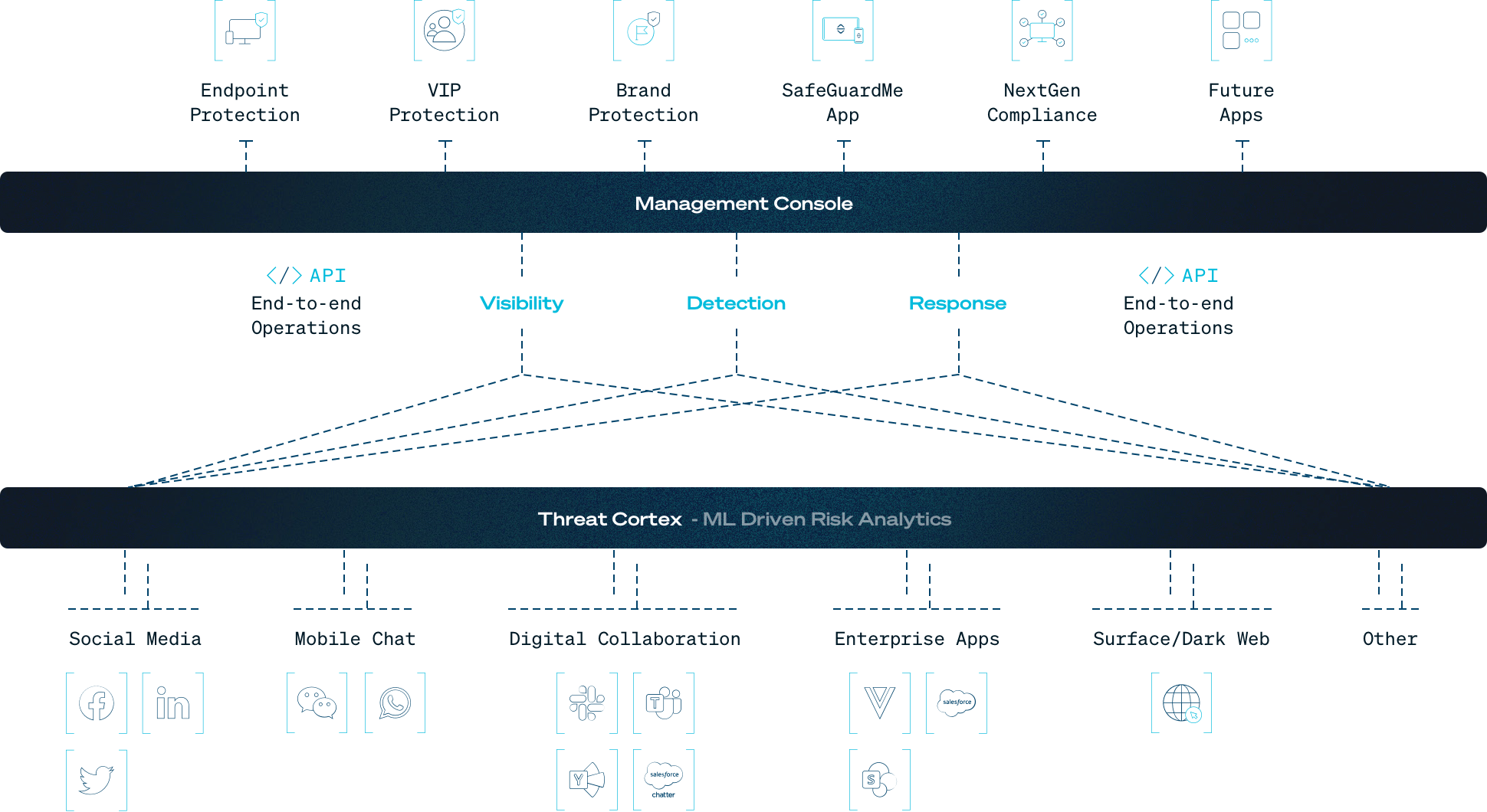
Security teams need an effective, robust solution that detects social engineering attacks in the cloud workspace – one that’s capable of providing:
 1. Enhanced visibility
1. Enhanced visibilityComplete business communications visibility through direct API integrations with popular applications. Unified view of threat and risk indicators across SaaS collaboration and communication applications.
Disrupt the kill chain early by detecting the interactions that indicate early stages of spear phishing, social engineering, and attacks on communication channels.
The cloud workspace needs to be supervised 24/7 for suspicious activity and messaging. All fields, attachments, and links should be automatically scanned for malware, including ransomware, and connections should be evaluated for known or suspicious actors.
Integrations with existing SIEM platforms can expose social engineering threats and collaboration security events quickly and move them into existing IR workflows.
Advanced threat protection on social networks without invading employee privacy by masking their message content.
 6. Natural language understanding
6. Natural language understandingCommunications-based risk analytics to detect and respond to patterns, context, and intent of communications across different languages.

SafeGuardCyber Survey April, 2019
SafeGuardCyber Survey April, 2019
Lorem ipsum dolor
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nulla urna massa, maximus at neque vel, mollis efficitur.
Benefits
With SafeGuard Cyber’s agentless architecture, organizations benefit from:
Gain unprecedented visibility to respond to internal and external threats in hard-to-see places like direct messages and group channels. Reduce detection and response times in the cloud infrastructure where work gets done.
Be up and running in hours not days. Organizations no longer have to configure agents.
Connect our agentless security platform into your existing cyber defense systems, feeding event data and telemetry into your EDR and SIEM solutions.
Combating Social Engineering with NLU
Humans can’t be relied upon to read and filter every message passing through these communication channels. Expanding cybersecurity across the enterprise requires the help of natural language understanding (NLU). FirstSight’s integration of NLU aids in analyzing and pinpointing social engineering attempts with high accuracy, making it a vital component in modern cybersecurity strategies.
Whether the language is spoken or written, natural language understanding uses machine learning to take real-world input, process it, and make sense of it with advanced probabilistic modeling.
SafeGuard Cyber security researchers have established a novel machine learning-based model that detects social engineering attacks through Natural Language Understanding across communications channels, protecting accounts from business communication compromise (BCC).
This social engineering detection model identifies potential threats by scanning and identifying key attributes of text and content that can suggest an upcoming attack. Determinants like a sense of urgency or discussions around payment or credentials are key components of an imminent social engineering attack.

Natural Language Understanding (NLU)
It is the ability of a computer program to understand human language as it is spoken and written – referred to as natural language. It is a component of artificial intelligence (AI).
---
Repelling the Social Engineers
Social engineers have increasingly targeted both employees and executives in this era of remote work, using workspace channels as their “entrances” to their business systems.
The costs are too high: EA data was ransomed for $28M but considering the company’s market cap, it could now be worth billions. The cost is not just measured in dollars, but in the brand and reputational damage that these attacks can incur in an organization.
Too often, key employees and executives at many organizations rely on security awareness training rather than actual security controls. While training is a necessary element, it cannot be the only thing an organization relies upon to thwart social engineering’s destructive effects.
For these reasons, companies need cybersecurity systems with intuitive controls, enhanced visibility, advanced threat detection, rapid incident response, and natural language understanding.
With these capabilities, businesses can proactively detect digital interactions that indicate the early stages of social engineering and workspace channel attacks, securing their systems and deploying an important step forward to a zero trust security model.
This approach can secure an organization’s investments and their sensitive data as well as offer protection for the company’s future. Resilience against social engineering and other cyberthreats is no longer a luxury; it’s a necessity.

Secure Human Connections
Ready to see how SafeGuard Cyber secures modern communication apps wherever they exist?
Expert Insights on Cloud App Risks
Stay up-to-date on the latest insider threats, ransomware, and third-party vulnerabilities.



